Imagine a bustling airport where planes take off continuously—each representing a software release. The air traffic control (ATC) system, responsible for coordinating every takeoff, is a blend of precision, timing, and safety checks. DevSecOps works much the same way, ensuring that software flies safely from development to deployment without collisions or vulnerabilities.
In today’s continuous delivery world, where speed is everything, embedding security automation directly into the CI/CD pipeline has become a necessity rather than an afterthought. This is where Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) take centre stage—two complementary tools acting as security radars for the software “flight path.”
The Evolution from DevOps to DevSecOps
Traditional DevOps focused on collaboration, automation, and continuous delivery—bridging the once-separated worlds of development and operations. But as organisations accelerated release cycles, vulnerabilities began slipping through undetected, turning agility into risk. DevSecOps emerged to weave security into the very fabric of DevOps, ensuring protection evolves hand in hand with innovation.
Think of it as adding a “security pit crew” to a Formula 1 race. The cars (applications) still move fast, but every lap includes automated safety checks that keep performance and protection in perfect balance.
Professionals mastering these practices through structured learning, such as a devops training in chennai, often find that the key is not slowing down to secure applications, but automating security so it accelerates alongside development.
SAST: The Code Whisperer
Static Application Security Testing (SAST) acts like a seasoned editor reviewing a manuscript before it’s published. It scans the source code or binaries early in the development cycle—before the application is even compiled—to identify vulnerabilities such as injection flaws, buffer overflows, or insecure coding patterns.
Because SAST examines the code without executing it, developers gain early visibility into potential weaknesses long before the software reaches production. This proactive nature makes it invaluable in preventing defects from propagating downstream, where fixes become more expensive and time-consuming.
For example, integrating SAST tools like SonarQube, Checkmarx, or Fortify into the CI/CD pipeline allows every commit or pull request to trigger automated scans. If vulnerabilities exceed defined thresholds, the pipeline halts, giving developers immediate feedback. This transforms security from a separate phase into a real-time conversation—one where every code push is vetted automatically.
However, SAST has limitations. It can struggle with issues that arise only during runtime, and its static nature sometimes generates false positives. This is where DAST complements the story.
DAST: The Ethical Hacker Inside Your Pipeline
If SAST is the careful editor, DAST is the ethical hacker probing the application once it’s live. Instead of examining source code, DAST interacts with the running application, simulating real-world attacks like SQL injections, authentication flaws, and cross-site scripting.
Picture a fire drill for your software—DAST identifies how your application behaves under pressure. It doesn’t need access to source code; instead, it tests how the system responds to external input. Tools like OWASP ZAP, Burp Suite, and Acunetix emulate an attacker’s mindset, providing insights into vulnerabilities that static analysis might miss.
When automated within the CI/CD pipeline, DAST can run nightly or post-deployment scans, offering continuous assurance that newly integrated code hasn’t introduced exploitable weaknesses. Together, SAST and DAST create a dual defence mechanism—one analysing from within, the other from outside.
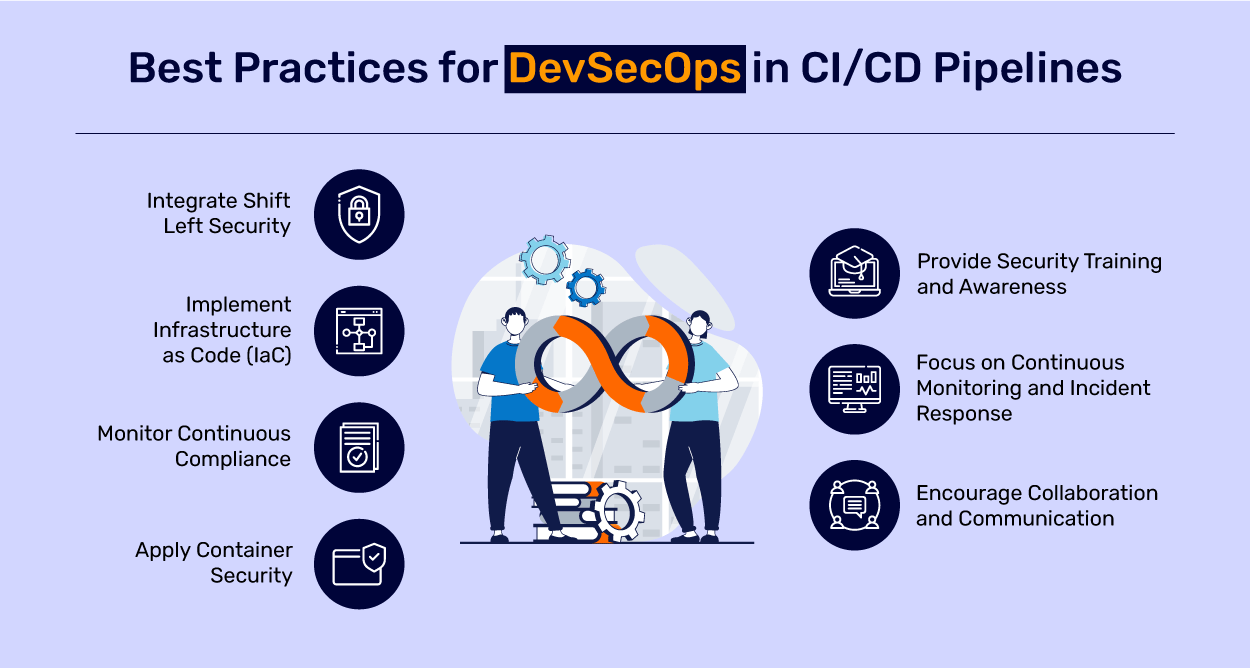
Integrating Security into the CI/CD Pipeline
Embedding SAST and DAST into CI/CD isn’t just about plugging in tools—it’s about reengineering workflow philosophy. Every stage of the pipeline becomes a checkpoint for safety. Here’s how organisations make it work:
- Source Stage (SAST): As developers commit code, automated SAST scans run in the background. Results feed directly into dashboards, alerting teams instantly about critical issues.
- Build and Test Stage: SAST findings guide developers to fix issues before merging. Meanwhile, unit tests validate that patches haven’t broken functionality.
- Staging Stage (DAST): Once the application is deployed to a testing environment, automated DAST scans simulate attacks to ensure runtime resilience.
- Release and Deploy: If both static and dynamic checks pass, the build moves forward confidently, carrying an assurance of security at both the code and execution levels.
By integrating both layers seamlessly, organisations turn their CI/CD pipelines into intelligent gatekeepers—ones that automatically assess, learn, and evolve with every deployment.
The Role of Automation and AI in DevSecOps
The real power of DevSecOps automation lies in scale and intelligence. Modern pipelines can analyse thousands of lines of code, correlate vulnerabilities with risk scores, and even prioritise fixes based on exploit probability. Machine learning algorithms detect recurring issues, allowing teams to anticipate vulnerabilities before they arise.
Automation doesn’t replace security engineers—it amplifies them. Developers become empowered to build secure code by default, while operations teams gain visibility into compliance without manual intervention. Together, AI-driven security and continuous delivery converge to create systems that are both fast and fortified.
Professionals who undergo specialised programs such as devops training in chennai learn to design such integrated architectures, blending security intelligence with automation pipelines to create frictionless and fail-safe delivery ecosystems.
Conclusion
In the race toward digital innovation, security can no longer be the checkpoint at the end—it must be the guardrail that runs alongside the entire journey. By embedding SAST and DAST directly into CI/CD pipelines, organisations achieve the perfect balance between velocity and vigilance.
DevSecOps automation doesn’t just make security faster—it makes it smarter. It ensures every code commit, build, and deployment is a calculated step forward, not a leap into uncertainty. In a world where vulnerabilities evolve daily, continuous delivery must also mean continuous protection—and that is the true promise of automated security in modern DevOps ecosystems.